An extremely silly bug
🐞
It was one in the morning. I was coding a JavaScript front-end calling an API. Every time I hit the load data button, in addition to loading the data, the browser’s print dialogue would open. Like this.
I was suspicious, because I'd used a 3rd party slugify function with unicode regex that I didn’t really understand:
slug = slug.normalize('NFD').replace(/[\u0300-\u036f]/g, '')Malware? I read about code almost this innocent-looking containing obfuscated malware-delivery, and also about researchers finding code snippets in the wild that display differently from what gets copy-and-pasted, so people might read them, and then paste and run them without re-reading them, and suddenly discover that they're curl-ing to bash and uploading all their SSH keys and crypto wallets.
I was also paranoid because I hand-code pretty much all my software without LLM assistance, but for this one-off script (gathering data for an Autodidacts newsletter, and not using any auth or non-public data) I'd generated the boilerplate code with an LLM.
The answer, as foreshadowed by the title, was much more embarrassing and funny.
I had been writing a lot of Python. And I had added some logging to make sure the slugify function was working properly...

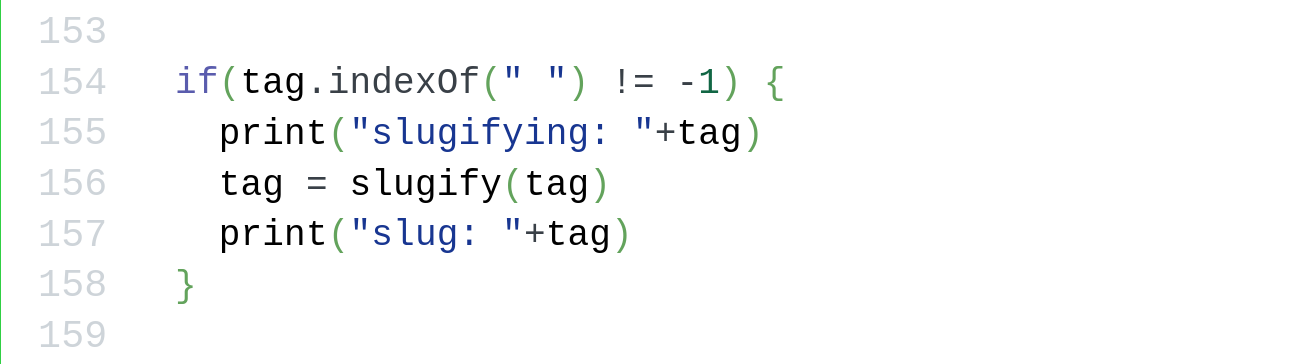
That’s right. I had used Python’s print("Message") for logging instead of JavaScript’s console.log("Message"). And, guess what print() does in JavaScript!
